Network Security
1. What is Network Security?

Network Security Network security refers to the protection of computer networks and their infrastructure from unauthorized access, misuse, modification, or destruction. It involves a combination of hardware, software, policies, and practices to ensure the confidentiality, integrity, and availability (CIA) of data transmitted across networks. Organizations implement network security to safeguard sensitive information, prevent cyberattacks, and maintain system reliability. Common threats to network security include malware, phishing, denial-of-service (DoS) attacks, man-in-the-middle (MITM) attacks, and data breaches
Key components of network security include firewalls, intrusion detection and prevention systems (IDPS), virtual private networks (VPNs), and encryption. Firewalls act as gatekeepers, filtering incoming and outgoing traffic based on security rules. IDPS monitor network traffic for suspicious activities and take action against potential threats. VPNs create secure, encrypted channels for remote access, protecting data from interception. Encryption ensures that even if data is intercepted, it remains unreadable without the correct decryption key. Access control mechanisms, such as multi-factor authentication (MFA) and role-based access control (RBAC), restrict unauthorized user access.
With the rise of cloud computing, IoT, and 5G technologies, network security is becoming increasingly complex. Organizations adopt zero-trust architectures, where no user or device is automatically trusted. Regular security audits, vulnerability assessments, and penetration testing help identify and mitigate weaknesses. Artificial intelligence (AI) and machine learning (ML) are also enhancing network security by providing real-time threat detection and automated response systems. As cyber threats evolve, continuous monitoring, compliance with security standards (e.g., ISO 27001, GDPR), and user education play a vital role in maintaining a secure and resilient network environment.
2. Firewalls
Firewalls A firewall is a network security device or software that monitors and controls incoming and outgoing network traffic based on predefined security rules. It acts as a barrier between a trusted internal network (like a company's private network) and untrusted external networks (such as the internet). The primary function of a firewall is to allow legitimate traffic while blocking malicious or unauthorized access. Firewalls are a critical component of network security, helping protect systems from cyberattacks, data breaches, and unauthorized access.
Firewalls operate using various techniques, including packet filtering, stateful inspection, proxy services, and deep packet inspection (DPI). Packet filtering analyzes network packets and blocks or allows them based on rules like IP address, port number, and protocol type. Stateful inspection tracks the state of active connections to ensure packets are part of an established session. Proxy firewalls act as intermediaries between users and the internet, hiding internal networks from external entities. Deep packet inspection examines the content of packets to detect and block malware, intrusions, or sensitive data leaks.
There are different types of firewalls, including hardware firewalls, software firewalls, cloud-based firewalls, and next-generation firewalls (NGFWs). Hardware firewalls are physical devices placed between a network and the internet, ideal for large organizations. Software firewalls are installed on individual devices, providing personal protection. Cloud-based firewalls offer scalable protection for cloud infrastructure, while NGFWs combine traditional firewall functions with advanced capabilities like intrusion prevention systems (IPS) and application-layer filtering. Firewalls are essential for securing home networks, corporate systems, and data centers against cyber threats like DDoS attacks, ransomware, and unauthorized access.

3. Intrusion Detection Systems
Intrusion Detection Systems (IDS) are critical security tools that monitor network traffic for suspicious activities and unauthorized access. They help identify cyber threats, such as malware, hacking attempts, and policy violations in real-time. IDS work by analyzing traffic and comparing it with known attack patterns or identifying unusual behavior. There are two main types: Network-based IDS (NIDS) and Host-based IDS (HIDS). NIDS scans the entire network for threats, while HIDS monitors individual devices for anomalies. These systems can be passive, which means they only generate alerts, or active, which can take automated actions. IDS is a vital part of an organization’s cybersecurity strategy to prevent potential breaches.
Modern IDS utilize advanced technologies like machine learning and behavioral analysis to detect sophisticated attacks and zero-day vulnerabilities. These techniques allow IDS to identify unusual patterns that may not match known attack signatures. Organizations often combine IDS with other security tools like firewalls and intrusion prevention systems (IPS) for comprehensive protection. Regularly updating the IDS ensures it can detect emerging threats effectively. In large networks, IDS are essential to monitor traffic flow and identify potential weaknesses. This proactive approach helps organizations maintain a secure and resilient infrastructure.
The effectiveness of an IDS depends on proper configuration, continuous monitoring, and timely updates. Security teams must analyze IDS alerts to distinguish between false positives and genuine threats. By integrating IDS with security information and event management (SIEM) systems, organizations can get a centralized view of their network security. This allows for faster response times and better threat detection. As cyberattacks become more advanced, having a robust IDS is crucial to safeguarding sensitive information. Regular testing and evaluation of IDS performance help maintain network integrity and protect critical assets.
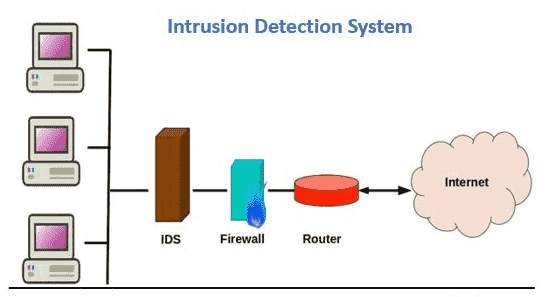
4. Network Segmentation
Network Segmentationis a security practice that involves dividing a computer network into smaller, isolated sections or segments. This helps control traffic flow, enhance security, and improve performance. By limiting communication between segments, organizations can prevent unauthorized access to sensitive areas and reduce the impact of a cyberattack. For example, in a business network, user devices, servers, and guest Wi-Fi can be separated to protect critical resources. This approach minimizes the risk of lateral movement, where an attacker spreads across the network after gaining access.
There are different types of network segmentation, including physical and logical segmentation. Physical segmentation involves using separate hardware, such as different switches and routers, for each network segment. Logical segmentation uses technologies like Virtual LANs (VLANs) and subnets to divide a network while sharing the same physical infrastructure. Micro-segmentation is an advanced form of logical segmentation that isolates workloads at the application level. This is particularly useful in cloud environments and data centers, where granular control over data flows is required.
Effective network segmentation provides several benefits, including improved security, better network performance, and simplified compliance with industry regulations. It helps contain threats by limiting the spread of malware and restricting unauthorized access. Segmentation also allows organizations to prioritize critical systems and reduce congestion by managing traffic more efficiently. Implementing and maintaining proper network segmentation requires careful planning, regular monitoring, and consistent updates to address new security risks. This layered defense approach is essential for protecting sensitive data and maintaining business continuity in modern IT environments.
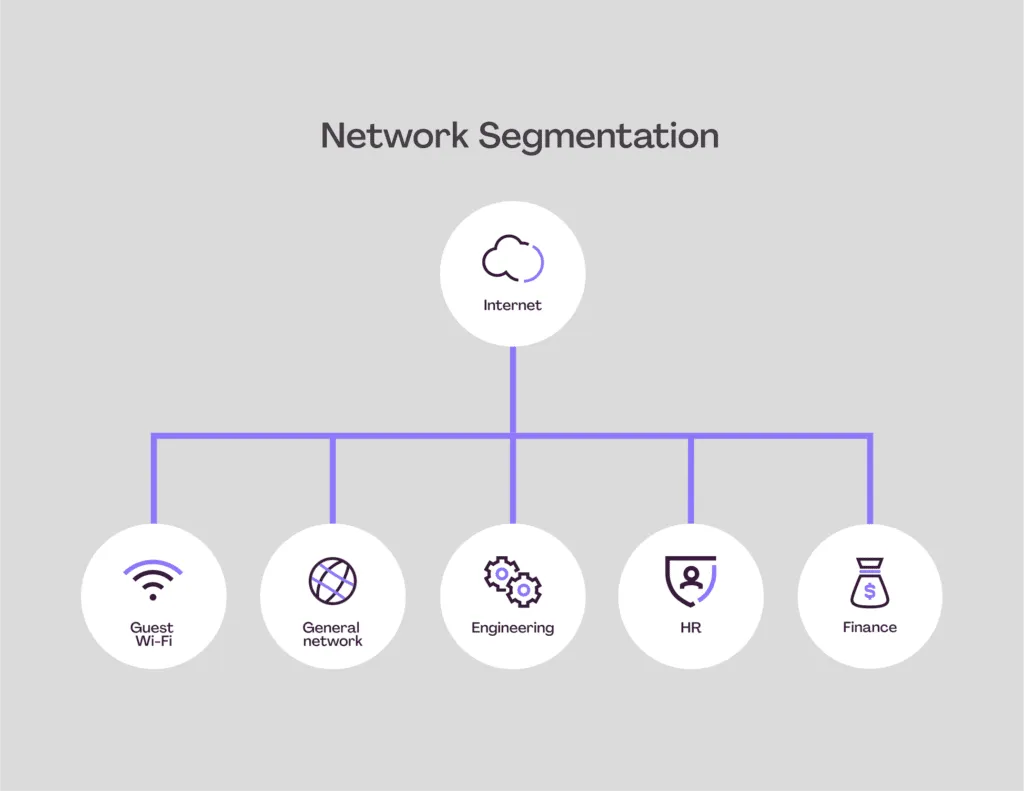
5.Secure Wi-Fi Protocols
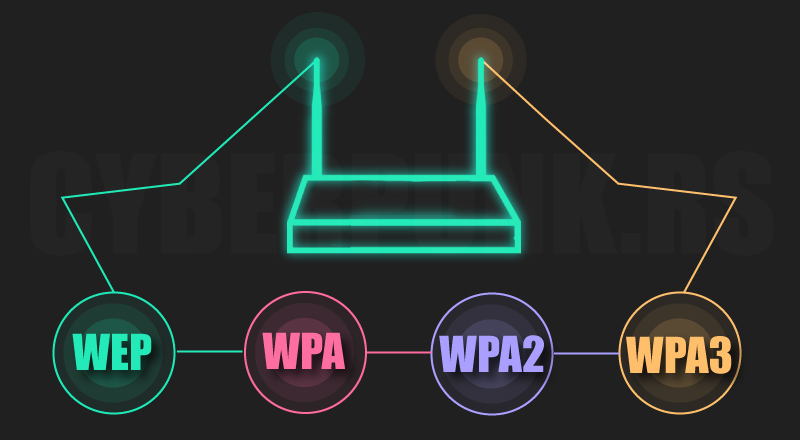
Secure Wi-Fi protocols are encryption standards that protect wireless networks by ensuring that data transmitted between devices and routers is confidential and secure. These protocols prevent unauthorized access, data interception, and cyberattacks on wireless networks. The most commonly used secure Wi-Fi protocols include WEP (Wired Equivalent Privacy), WPA (Wi-Fi Protected Access), WPA2, and WPA3. Each protocol has evolved to address vulnerabilities in previous versions, with WPA3 being the most secure and modern standard, providing stronger encryption and better protection against brute-force attacks.
WEP was the first Wi-Fi security protocol, but it is outdated and easily hackable due to weak encryption methods. WPA improved on WEP by using Temporal Key Integrity Protocol (TKIP), offering better encryption but still having vulnerabilities. WPA2, introduced in 2004, became the industry standard and uses Advanced Encryption Standard (AES), which provides strong security and is widely used in homes and businesses. However, WPA2 is vulnerable to KRACK (Key Reinstallation Attacks) if not properly updated. WPA3, introduced in 2018, enhances security with 128-bit encryption, forward secrecy, and protected management frames (PMF), offering better defense against modern cyber threats.
Using secure Wi-Fi protocols is crucial for protecting sensitive information, especially in public and corporate environments. It is recommended to use WPA3 wherever possible, or WPA2 if devices are not compatible with the latest standard. Additional security measures like disabling WPS (Wi-Fi Protected Setup), using strong passwords, and enabling network segmentation further enhance Wi-Fi security. Regularly updating router firmware and monitoring connected devices can help maintain a secure wireless environment. Adopting the latest secure Wi-Fi protocols ensures safe communication, protects user privacy, and reduces the risk of cyberattacks.
6. VPNs
VPNs(Virtual Private Networks) are secure communication technologies that create an encrypted tunnel between a user's device and the internet, ensuring privacy, security, and anonymity online. VPNs protect data by encrypting it before it leaves the device, making it difficult for hackers, ISPs (Internet Service Providers), or third parties to intercept or monitor online activities. This is especially useful when using public Wi-Fi networks, where data is more vulnerable to cyberattacks. VPNs also allow users to mask their IP addresses, making their online presence anonymous and helping them bypass geo-restrictions to access content from different regions.
There are different types of VPNs, including Remote Access VPNs, Site-to-Site VPNs, and SSL/TLS VPNs. Remote Access VPNs are commonly used by individuals to securely connect to private networks over the internet, ideal for remote work. Site-to-Site VPNs connect entire networks, allowing businesses to link branch offices securely. SSL/TLS VPNs enable secure access through a web browser, eliminating the need for specialized client software. VPN protocols such as OpenVPN, IPSec, L2TP, and WireGuard determine how data is encrypted and transmitted, each offering varying levels of speed and security.
Using a VPN offers several advantages, including enhanced privacy, data protection, and access to restricted content. It is useful for protecting sensitive information like banking details or personal communications from cyber threats. However, VPNs can sometimes reduce internet speed due to encryption processes and may not be compatible with all services. It is important to choose a reputable VPN provider with a no-log policy, strong encryption standards, and multi-platform support for better security. In today’s digital world, VPNs are essential tools for ensuring online safety and maintaining privacy in both personal and professional environments.

7. Zero Trust Architecture
Zero Trust Architecture is a modern cybersecurity framework based on the principle of "never trust, always verify." Unlike traditional security models that assume everything within the network is safe, ZTA requires continuous verification of all users, devices, and applications—whether inside or outside the network. This approach minimizes the risk of unauthorized access and data breaches by implementing strict access controls and monitoring all activities. Every request for access is verified based on factors such as user identity, device health, and location, ensuring that only legitimate users can interact with sensitive data and resources.
A Zero Trust framework typically includes several core components, such as multi-factor authentication (MFA), least privilege access, micro-segmentation, and continuous monitoring. MFA ensures that users must provide multiple forms of identification before gaining access. Least privilege access limits user permissions to only what is necessary for their tasks, reducing the potential impact of compromised accounts. Micro-segmentation involves dividing the network into smaller, isolated sections to prevent lateral movement by attackers. Continuous monitoring tracks all network activity in real-time, enabling quick detection and response to potential threats.
Implementing Zero Trust Architecture offers several benefits, including improved security, reduced attack surfaces, and better regulatory compliance. It helps protect sensitive information, even when users access the network remotely, making it ideal for hybrid work environments. Organizations adopting ZTA must assess their digital assets, enforce strict identity verification, and apply advanced security controls across all endpoints. As cyber threats become more sophisticated, Zero Trust is becoming a critical approach for ensuring data security and protecting critical systems in modern enterprises.
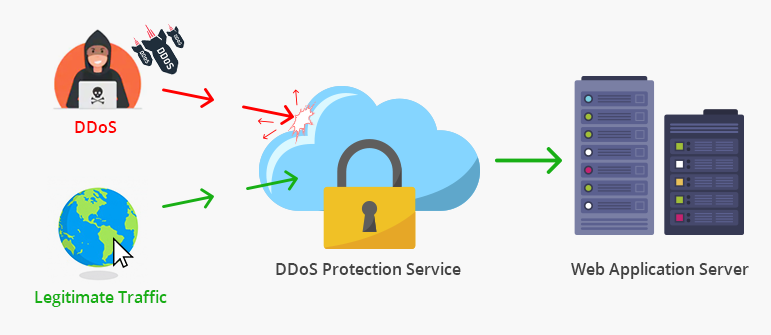
8. DDoS Protection
DDoS (Distributed Denial-of-Service) Protection refers to the methods and technologies used to prevent, detect, and mitigate DDoS attacks. A DDoS attack occurs when multiple compromised systems flood a targeted server, service, or network with overwhelming traffic, causing disruptions or making resources inaccessible. DDoS protection aims to maintain the availability and performance of online services by filtering or blocking malicious traffic while allowing legitimate users to access the system. It is essential for businesses and organizations to safeguard their digital presence and ensure uninterrupted operations.
Effective DDoS protection involves using a combination of network-level defenses and application-level strategies. This includes traffic analysis, rate limiting, and IP filtering to detect and block unusual activity. Content Delivery Networks (CDNs) and load balancers help distribute traffic across multiple servers, reducing the impact of an attack. Additionally, cloud-based DDoS protection services offer scalable and real-time mitigation by diverting malicious traffic before it reaches the target. Firewalls and Intrusion Prevention Systems (IPS) also play a crucial role in identifying and blocking suspicious requests.
To maintain robust DDoS protection, organizations must implement a multi-layered defense strategy and perform regular testing of their systems. Early detection is critical, and anomaly-based monitoring can identify abnormal traffic patterns. Incident response plans ensure quick mitigation in case of an attack. Advanced machine learning algorithms also help predict and block sophisticated DDoS threats. As cyberattacks continue to evolve, DDoS protection is a key element of modern cybersecurity frameworks, ensuring the continuous availability and reliability of online services.
Comments