Cloud Security
1. what is Cloud Security?

Cloud Security refers to the policies, technologies, and practices designed to protect data, applications, and infrastructure in cloud environments. Since cloud services store and process sensitive information over the internet, securing these resources is essential to prevent unauthorized access, data breaches, and cyberattacks. Cloud security involves user access controls, data encryption, threat monitoring, and incident response to ensure the confidentiality, integrity, and availability of cloud-based assets.
One of the key aspects of cloud security is data protection. This includes encrypting data while it is being stored (at rest) and during transmission (in transit). Encryption ensures that only authorized users can access sensitive information. Additionally, access control mechanisms like multi-factor authentication (MFA) and identity management limit who can view or modify cloud resources.
Compliance is also a significant concern in cloud security. Organizations must follow legal and industry regulations such as GDPR, HIPAA, and ISO/IEC 27001 to ensure that customer data is handled securely. Cloud providers often offer certifications to demonstrate their compliance with these standards, but businesses must also ensure their internal processes align with legal requirements.Cloud security also includes threat detection and incident response. Security Information and Event Management (SIEM) tools monitor cloud environments in real-time to detect suspicious activities like unauthorized logins or data exfiltration. When a threat is identified, automated systems can alert security teams or even block the activity immediately to reduce potential damage.
2.Identity & Access Management (IAM)
Identity & Access Management (IAM) Identity & Access Management (IAM) is a framework of policies, technologies, and processes used to manage digital identities and control user access to systems, applications, and data. It ensures that the right users have the appropriate access to resources while keeping unauthorized users out. IAM is essential for maintaining security, compliance, and efficient user management in both on-premise and cloud environments.
A key feature of IAM is user authentication, which verifies a user’s identity before granting access. This can be done through methods like passwords, biometrics (fingerprint or facial recognition), or multi-factor authentication (MFA), which adds an extra layer of security. Once authenticated, authorization determines what resources a user can access based on their permissions and role within the organization.Another crucial component of IAM is role-based access control (RBAC). It assigns permissions based on user roles rather than individual identities. For example, an HR employee may have access to personnel records, while a developer can access code repositories. This minimizes the risk of over-permissioned users and limits access to only what is needed for their job.
IAM systems also include user provisioning and de-provisioning. When a new employee joins, IAM automatically grants the necessary access rights. Similarly, when an employee leaves, their access is revoked to prevent security risks. This automation reduces human error and ensures that users only have access while they are actively part of the system.
4.jpeg)
3. Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM)
is a set of tools and practices designed to help organizations monitor, identify, and remediate security risks across cloud environments. As businesses increasingly adopt cloud services, maintaining a strong security posture becomes essential to protect sensitive data and maintain compliance. CSPM solutions continuously scan cloud infrastructures to detect misconfigurations, policy violations, and security gaps that could lead to data breaches. These tools automate the process of monitoring complex, multi-cloud environments to ensure that organizations follow best practices and security standards like ISO 27001, HIPAA, and GDPR.
A key function of CSPM is misconfiguration detection and remediation. Cloud environments are dynamic, and human error or oversight can lead to security vulnerabilities, such as open storage buckets, unrestricted access policies, or weak authentication mechanisms. CSPM tools identify these risks in real time and provide actionable insights to fix them. For example, if a storage bucket is inadvertently made public, CSPM can alert administrators and suggest steps to restrict access. This automated monitoring reduces manual effort and ensures that security policies are consistently applied across all cloud resources.
Another crucial aspect of CSPM is compliance management. Organizations in regulated industries must follow strict guidelines to protect user data. CSPM tools offer continuous compliance monitoring by mapping cloud configurations against industry standards. This helps businesses quickly identify and address non-compliance issues and generate audit-ready reports. By maintaining an up-to-date security posture, companies can avoid fines, legal issues, and reputational damage. Furthermore, CSPM enhances incident response by providing visibility into cloud assets and facilitating quicker identification and mitigation of potential threats. This proactive approach helps maintain data integrity, availability, and confidentiality in the cloud.
.webp)
4.Cloud-native Security
Cloud-native Security
refers to a specialized approach to protecting applications, data, and infrastructure that are built and operated in cloud environments. Unlike traditional security methods, which are designed for on-premise systems, cloud-native security is tailored to the dynamic and scalable nature of the cloud. It emphasizes automation, continuous monitoring, and microservice protection to safeguard cloud-based workloads. This approach integrates security throughout the development lifecycle, ensuring that security is not just an afterthought but a core component from design to deployment. Cloud-native security tools are designed to operate across multi-cloud and hybrid environments, providing comprehensive visibility and protection.
A critical aspect of cloud-native security is container and Kubernetes security. Modern cloud applications often use containers for better efficiency and scalability, but they also introduce new security risks. Cloud-native security solutions monitor container activities, check for vulnerabilities, and enforce access controls to prevent unauthorized operations. Kubernetes, an orchestration platform for managing containers, requires network segmentation, identity-based policies, and runtime protection. Cloud-native security ensures that these containerized workloads are protected against malicious attacks, data breaches, and misconfigurations, while also maintaining compliance with industry regulations
Another key element of cloud-native security is DevSecOps—the integration of security into the software development and operations process. This approach enables security checks and vulnerability scanning to be conducted at every stage of the CI/CD (Continuous Integration/Continuous Deployment) pipeline. By automating security testing and policy enforcement, organizations can detect and remediate vulnerabilities before applications reach production. Additionally, cloud-native security leverages zero-trust architecture, which assumes no implicit trust and requires verification for every user and system access request. This comprehensive security framework helps organizations respond to evolving cyber threats while ensuring the scalability and agility of their cloud-native applications.

5.Data Encryption in Cloud
Data Encryption in Cloud
is a critical security measure that protects sensitive data by converting it into an unreadable format, ensuring that only authorized users with the correct decryption key can access it. This process safeguards data both at rest (stored data) and in transit (data being transferred between systems). Cloud providers use advanced encryption algorithms such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) to protect data from unauthorized access and cyber threats. Encryption ensures that even if data is intercepted or stolen, it remains inaccessible without the decryption key, maintaining the confidentiality and integrity of sensitive information.
One essential component of cloud data encryption is client-side and server-side encryption. In client-side encryption, data is encrypted before being uploaded to the cloud, and only the client holds the decryption keys. This approach provides greater control over data privacy but requires advanced management of encryption keys. Server-side encryption, on the other hand, encrypts data once it reaches the cloud provider’s servers. Cloud providers typically manage the encryption and decryption processes using their own key management systems (KMS). While this method is easier to implement, it relies on the provider's infrastructure for data security, making it important to choose trusted cloud vendors with strong encryption policies.
Effective key management is crucial for secure cloud encryption. Encryption is only as strong as the protection of the encryption keys, which are used to lock and unlock data. Many cloud providers offer KMS (Key Management Services) that allow businesses to create, rotate, and control their encryption keys securely. Some organizations use bring your own key (BYOK) or hold your own key (HYOK) models to retain full ownership and control of their encryption keys. Proper key lifecycle management, including generation, rotation, and revocation, is vital to maintaining data privacy and ensuring compliance with regulatory standards like GDPR and HIPAA in cloud environments.
6.Shared Responsibility Model
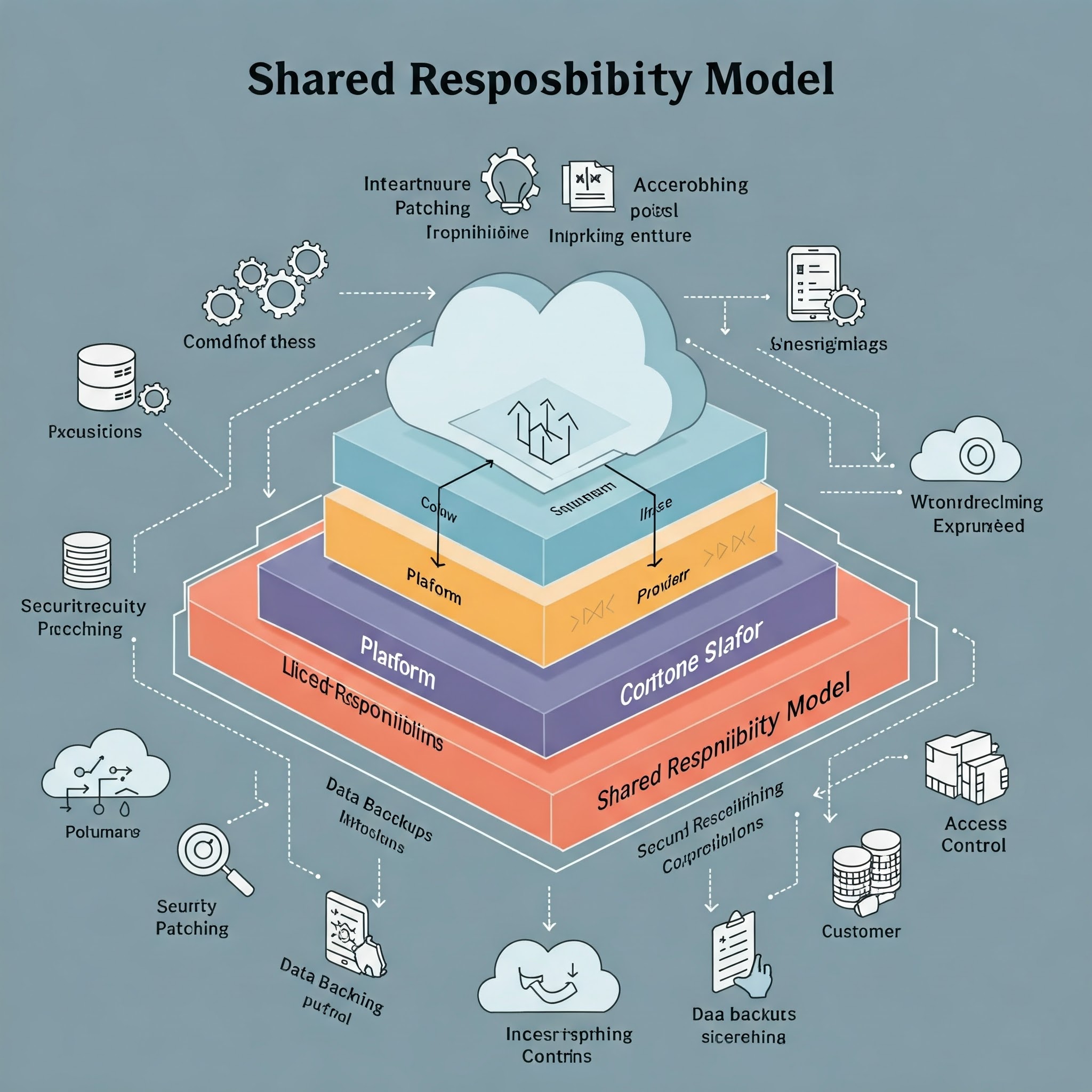
Shared Responsibility Model
in cloud computing defines the security responsibilities shared between the cloud service provider (CSP) and the customer. This model ensures that both parties play a role in maintaining a secure cloud environment. Cloud providers are responsible for securing the cloud infrastructure, including hardware, software, networking, and physical data centers. On the other hand, customers are responsible for securing their data, applications, and access controls within the cloud environment. This clear division of responsibility helps prevent security gaps and ensures a collaborative approach to safeguarding sensitive information.
In Infrastructure as a Service (IaaS), the customer holds more responsibility for managing the operating system, applications, and data security, while the provider manages the physical infrastructure and network security. In Platform as a Service (PaaS), the cloud provider takes care of the infrastructure and runtime environment, while customers handle their applications and data protection. In Software as a Service (SaaS), the provider manages almost everything, including infrastructure, software, and security, while customers focus on user access and data privacy. Understanding these responsibilities is crucial for maintaining security and ensuring compliance with regulations.
The Shared Responsibility Model also highlights the importance of data encryption, identity and access management (IAM), and security monitoring. Cloud customers must ensure proper configuration of cloud services and enforce access controls to prevent unauthorized access. Cloud providers, in turn, ensure uptime, physical security, and patching of underlying systems. Organizations that follow the Shared Responsibility Model can reduce the risk of data breaches, improve incident response, and maintain compliance with standards such as GDPR, HIPAA, and ISO 27001. This collaborative approach is essential for achieving a secure and resilient cloud environment.
7. Compliance & Regulations
Compliance & Regulations
in cloud computing refer to the legal and industry standards that organizations must follow to protect sensitive data and ensure secure operations. As cloud adoption increases, adhering to these regulations becomes crucial for maintaining data privacy, security, and transparency. Various regulatory frameworks, such as GDPR (General Data Protection Regulation) in Europe and HIPAA (Health Insurance Portability and Accountability Act) in the United States, outline specific guidelines for handling personal and healthcare data. Organizations using cloud services must ensure that their cloud providers comply with these regulations and implement robust data protection measures to avoid legal penalties and reputational damage.
One of the primary concerns in cloud compliance is data residency and sovereignty. Many regulations require that data be stored and processed within specific geographic regions. For example, GDPR mandates that personal data of EU citizens remain within the European Union, while CCPA (California Consumer Privacy Act) focuses on the protection of consumer information in California. Cloud service providers must offer solutions that support data localization and provide tools for auditing and tracking data movement. Compliance also involves access control, encryption, regular audits, and incident reporting, ensuring that organizations can monitor and protect sensitive data effectively.
To maintain compliance, organizations must adopt best practices such as data classification, user access management, and encryption for data at rest and in transit. Many cloud providers offer compliance certifications like ISO 27001, SOC 2, and FedRAMP, which help customers verify the provider's security and regulatory standards. Implementing a Cloud Security Posture Management (CSPM) solution can automate compliance checks and identify misconfigurations. By following these practices and staying updated on regulatory changes, organizations can reduce legal risks, build customer trust, and ensure secure cloud operations while meeting compliance obligations across different regions and industries.

8.Cloud Workload Protection
Cloud Workload Protection refers to the security practices and solutions designed to safeguard workloads running in cloud environments. A "workload" in the cloud can include applications, virtual machines, containers, databases, and other services. As organizations migrate to the cloud, protecting these workloads from cyber threats becomes essential due to the dynamic and distributed nature of cloud computing. CWP solutions provide real-time monitoring, threat detection, and incident response to ensure workloads remain secure across public, private, and hybrid cloud environments. These systems detect vulnerabilities, enforce security policies, and safeguard against various attacks, such as malware, unauthorized access, and data breaches.
One of the primary functions of Cloud Workload Protection is vulnerability management. This involves continuously scanning workloads to identify and remediate software weaknesses that cybercriminals could exploit. CWP platforms also offer behavioral monitoring to track normal workload patterns and identify suspicious activities, such as unusual network traffic or file modifications. Additionally, micro-segmentation is used to restrict communication between different workloads, minimizing the risk of lateral movement if a breach occurs. This isolation strategy helps contain threats and prevents attackers from accessing critical systems and data.
Another key aspect of Cloud Workload Protection is compliance enforcement and automated threat response. CWP solutions ensure that cloud workloads adhere to industry regulations like GDPR, HIPAA, and PCI-DSS by enforcing security policies and maintaining audit trails. Automated threat response features can quickly isolate compromised workloads, remove malicious files, and alert security teams to mitigate damage. As cloud environments evolve, organizations must adopt multi-layered security approaches through Cloud Workload Protection Platforms (CWPP) to defend against advanced cyber threats, ensuring the integrity, availability, and confidentiality of their cloud-based assets.

Comments