Cryptography
1. What is Cryptography?
Cryptography is the practice of securing information by converting it into an unreadable format to prevent unauthorized access. It involves mathematical techniques and algorithms to encode (encrypt) and decode (decrypt) data, ensuring confidentiality, integrity, and authenticity. Cryptography is widely used in securing online communications, financial transactions, and sensitive information. For example, when you send a message through WhatsApp, it is encrypted so that only the recipient can read it, protecting your privacy from hackers or third parties.
Modern cryptography relies on various algorithms, including symmetric encryption and asymmetric encryption. Symmetric encryption uses a single key for both encryption and decryption, making it fast but requiring secure key sharing. Popular symmetric algorithms include AES (Advanced Encryption Standard). Asymmetric encryption, on the other hand, uses two keys—a public key for encryption and a private key for decryption—allowing secure communication without sharing the private key. RSA (Rivest-Shamir-Adleman) is a common asymmetric algorithm used in secure web browsing (HTTPS).
Cryptography also ensures data integrity and authenticity using hash functions and digital signatures. Hash functions, like SHA-256, convert data into a fixed-length hash value, allowing verification that data has not been tampered with. Digital signatures authenticate the sender's identity and ensure message integrity. Cryptography plays a critical role in modern cybersecurity, protecting everything from personal information and financial data to national security systems. As technology advances, new encryption methods are developed to counter emerging threats and ensure data remains secure.
2. Symmetric & Asymmetric Encryption
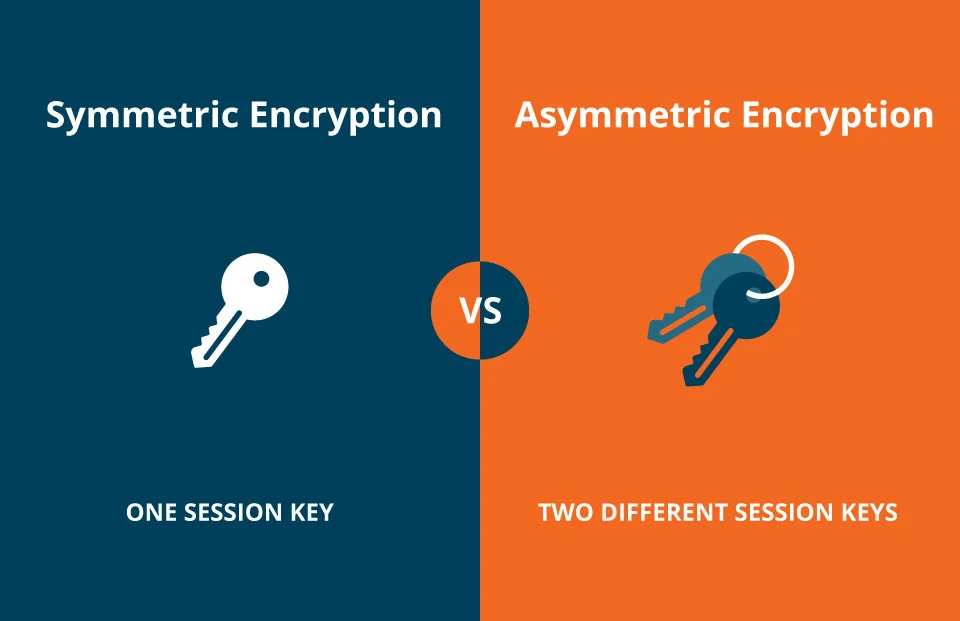
Symmetric & Asymmetric Encryption are two primary methods used to secure data through encryption. Both play crucial roles in ensuring data privacy and security but function differently in terms of key usage and applications.
Symmetric Encryption
Symmetric encryption uses a single key for both encryption (converting plain text into cipher text) and decryption (converting cipher text back to plain text). This method is fast and efficient, making it ideal for encrypting large amounts of data. However, the key must be securely shared between the sender and receiver, which can be a challenge. Common symmetric encryption algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard). For example, when you use a password to protect a ZIP file, symmetric encryption is used to lock and unlock the file.
Asymmetric Encryption
There are different types of penetration testing, including black-box, white-box, and gray-box testing. Black-box testing simulates an attack with no prior knowledge of the system, while white-box testing is conducted with full knowledge of the target’s internal architecture. Gray-box testing combines both approaches, providing partial access to information. Penetration testing is essential for organizations to identify and resolve security gaps, meet compliance standards, and protect sensitive data from cyber threats.
Differences Between Symmetric & Asymmetric Encryption
The main difference lies in key usage—symmetric encryption uses one key, while asymmetric encryption uses two keys. Symmetric encryption is faster but requires secure key sharing, while asymmetric encryption is slower but more secure without needing to exchange private keys. In practice, both methods are often combined—for example, in HTTPS, asymmetric encryption establishes a secure connection, and symmetric encryption handles the actual data transfer. This hybrid approach ensures both security and efficiency.
3. Hashing Algorithms
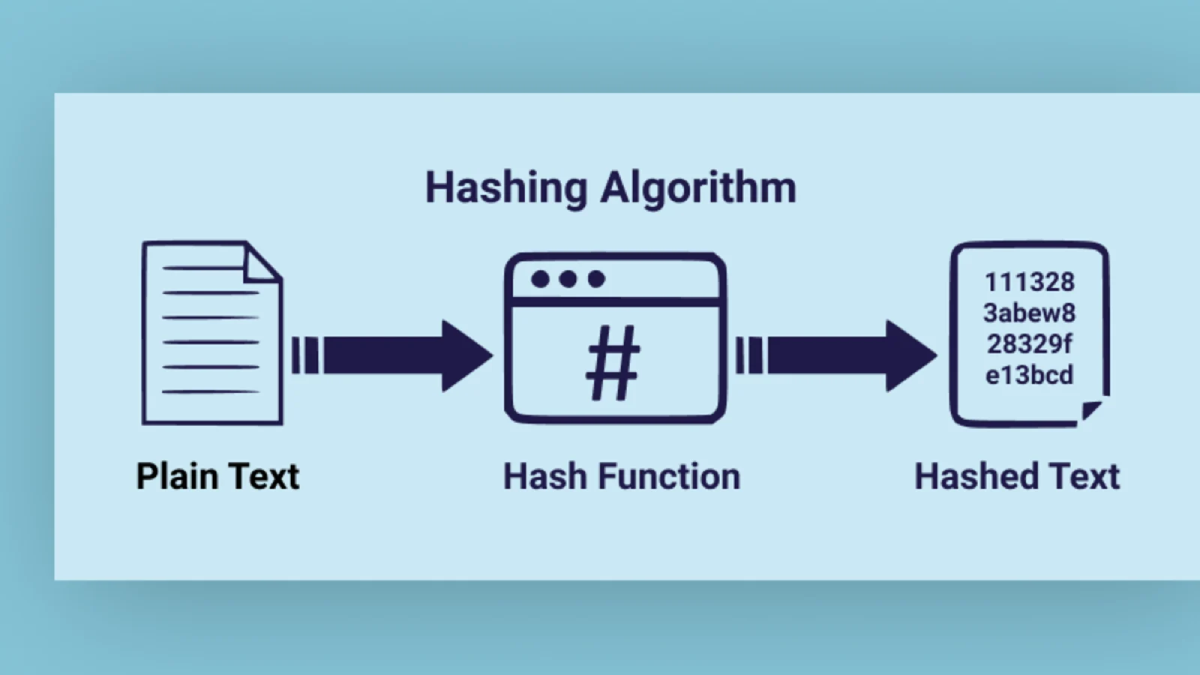
Hashing Algorithms are essential tools in cryptography that transform input data into a fixed-length string, known as a hash value or digest. These algorithms are one-way functions, meaning the original data cannot be reverse-engineered from the hash. They ensure data integrity by allowing users to verify that data has not been tampered with. MD5 and SHA (Secure Hash Algorithm) are popular hashing algorithms, though MD5 is considered weak due to collision vulnerabilities. Modern algorithms like SHA-256 are more secure and widely used in applications like blockchain and digital signatures. Hashing is also used for password protection, ensuring sensitive data remains safe during storage. This process plays a critical role in cybersecurity, ensuring data authenticity and system security.
In addition to securing passwords, hashing algorithms play a key role in digital forensics and data verification. When a file is hashed, even the smallest change in the data produces a completely different hash value, allowing systems to detect unauthorized modifications. For example, SHA-3 is an advanced hashing algorithm providing resistance to quantum computing attacks. Many online platforms use hashing for password storage, often combined with salting—adding a random value to each password before hashing—to enhance security. Secure hashing is crucial for digital certificates and cryptographic protocols, ensuring secure communication over networks. Blockchain relies on hashing for data immutability, making it impossible to alter past transactions without detection.
Modern hashing algorithms must balance speed and security to be effective across various applications. bcrypt and Argon2 are slow hashing algorithms specifically designed for password hashing, offering protection against brute-force and rainbow table attacks. These algorithms are widely used in modern systems because they can adjust their complexity over time to counter advances in computing power. Hashing is also vital for file integrity checks, where a file's hash is compared before and after transfer to ensure no corruption. Secure hashing techniques are continuously evolving to defend against new threats in cybersecurity. As technology advances, adopting more secure hashing algorithms remains critical for safeguarding sensitive information and digital systems.
4. Digital Signatures
Digital Signaturesare a type of cryptographic technique used to ensure the authenticity, integrity, and non-repudiation of digital data or electronic documents. They work by using public-key cryptography (asymmetric encryption) where a private key is used to sign the data, and a corresponding public key is used to verify the signature. When a sender signs a document, the signature is unique to both the message and the signer. If even a small change is made to the original message, the digital signature becomes invalid. This ensures the document's integrity and prevents tampering during transmission. Digital signatures are widely used in online transactions, legal documents, and software distribution to verify the authenticity of digital content.
The process of creating a digital signature involves generating a hash of the message using a hashing algorithm like SHA-256. This hash is then encrypted with the sender’s private key to create the signature. The recipient can verify the signature by decrypting it with the sender’s public key and comparing it with the hash of the received message. If the two match, it confirms the message’s authenticity and that it hasn’t been altered. Digital signatures provide non-repudiation, meaning the signer cannot later deny their involvement. This feature is crucial in legal contracts, banking systems, and government communications where data authenticity is critical.
Digital signature standards like PKCS#7, Digital Signature Algorithm (DSA), and RSA ensure secure implementation across platforms. Electronic signature laws such as eIDAS in Europe and ESIGN Act in the United States make digital signatures legally binding. They are also used in blockchain technology to verify transactions and ensure the authenticity of digital assets. Digital signatures enhance cybersecurity by protecting sensitive information from unauthorized access and forgery. As technology evolves, quantum-resistant digital signature algorithms are being developed to counter potential threats from future quantum computers. This ensures continued protection and trust in digital communications and electronic records.

5.Public Key Infrastructure (PKI)
Public Key Infrastructure (PKI) is a system of technologies, policies, and procedures used to create, manage, distribute, and revoke digital certificates and public-private key pairs. It is essential for ensuring secure communication over the internet by providing authentication, data integrity, and encryption. PKI relies on asymmetric cryptography, where a public key encrypts data, and a corresponding private key decrypts it. This method is widely used in online banking, email encryption, digital signatures, and website security (SSL/TLS). By verifying identities and ensuring that messages remain unchanged, PKI forms the backbone of modern digital security practices.
The core components of PKI include a Certificate Authority (CA), Registration Authority (RA), digital certificates, and certificate revocation lists (CRLs). The CA is a trusted entity that issues and verifies digital certificates, confirming the authenticity of the public key holder. The RA handles the process of verifying a user's identity before the CA issues a certificate. Digital certificates contain information like the public key, the certificate holder’s identity, and the certificate’s validity period. If a certificate is compromised or no longer valid, it is added to the CRL to prevent misuse. These components work together to establish a trust hierarchy for secure digital communication.
PKI is used in various applications, such as securing websites through SSL/TLS certificates, encrypting sensitive data, and digitally signing software to verify its authenticity. It also supports multi-factor authentication (MFA) and secure access to corporate networks. With the rise of IoT and cloud computing, PKI plays a critical role in safeguarding data across distributed environments. Modern PKI systems are adapting to new challenges, including quantum computing threats, by developing post-quantum cryptography. As technology evolves, PKI remains essential for maintaining trust, privacy, and data security in the digital world.
.jpg)
6. Blockchain Security
Blockchain Security refers to the practices and technologies used to protect blockchain networks, data, and transactions from cyber threats, unauthorized access, and vulnerabilities. Since blockchain is a decentralized and immutable system, ensuring its security is crucial to maintaining trust and data integrity. Security in blockchain involves protecting the consensus mechanism, cryptographic algorithms, and smart contracts from potential attacks. Common threats include 51% attacks, double-spending, and sybil attacks, where malicious actors try to manipulate the network. Implementing multi-layer encryption, access controls, and auditing procedures helps strengthen blockchain security and prevent unauthorized changes.
A key aspect of blockchain security is the use of cryptographic hashing and digital signatures to ensure data integrity and user authentication. Each block in the blockchain contains a cryptographic hash of the previous block, making it nearly impossible to alter data without changing every subsequent block. Smart contract security is another critical concern, as vulnerabilities in code can be exploited to steal funds or manipulate transactions. Regular code audits, formal verification, and bug bounty programs help identify and fix weaknesses in smart contracts. Permissioned blockchains, which limit participation to authorized users, provide an extra layer of security for businesses and enterprises handling sensitive information.
Blockchain networks also employ consensus algorithms like Proof of Work (PoW) and Proof of Stake (PoS) to validate transactions and maintain network integrity. These mechanisms prevent fraudulent activities by requiring significant computational work or asset staking. Privacy-focused techniques like zero-knowledge proofs (ZKPs) and confidential transactions further enhance security by concealing sensitive data. As blockchain technology evolves, post-quantum cryptography is being developed to protect against potential quantum computer threats. Ensuring blockchain security is essential for applications such as cryptocurrency, supply chain management, healthcare, and identity verification, safeguarding both digital assets and user privacy.
7. Post-Quantum Cryptography
Post-Quantum Cryptographyrefers to the development of cryptographic algorithms that can resist attacks from quantum computers. Traditional encryption methods, like RSA and ECC (Elliptic Curve Cryptography), rely on mathematical problems that are difficult for classical computers to solve. However, powerful quantum computers using Shor's algorithm can break these encryptions quickly, making sensitive data vulnerable. Post-quantum cryptography aims to design quantum-resistant algorithms that remain secure even against quantum computational threats. This field is crucial to protect digital communication, financial transactions, and personal information as quantum technology advances.
The most promising approaches in post-quantum cryptography include lattice-based cryptography, hash-based cryptography, code-based cryptography, and multivariate polynomial cryptography. Lattice-based methods rely on the complexity of solving problems in high-dimensional lattices, which are difficult for both classical and quantum computers. Hash-based cryptography uses secure hash functions to provide robust digital signatures. Code-based methods, like the McEliece cryptosystem, use error-correcting codes, while multivariate polynomial systems rely on solving complex polynomial equations. These approaches are being evaluated by organizations like NIST (National Institute of Standards and Technology) to standardize quantum-resistant algorithms.
The transition to post-quantum cryptography is essential for securing future communication systems, including online banking, government databases, and critical infrastructure. Implementing these algorithms requires upgrading current systems and ensuring backward compatibility with classical encryption. Large technology firms and government agencies are investing in quantum-safe protocols to prevent potential breaches once quantum computing becomes mainstream. The goal of PQC is to ensure that data remains protected against both classical and quantum threats, safeguarding global digital infrastructure in the future.
8. Secure Communications
Secure Communications refer to the methods and technologies used to protect data transmission from unauthorized access, interception, and tampering. This is crucial in personal, business, and government contexts to maintain confidentiality, integrity, and availability of information. Secure communication involves using encryption techniques, authentication protocols, and secure networks to safeguard messages and sensitive data. Technologies such as Transport Layer Security (TLS) and Secure Sockets Layer (SSL) encrypt data between devices, ensuring that only intended recipients can access the information. Secure communication is vital for protecting online activities like email, messaging, and financial transaction
Modern secure communication systems rely on advanced cryptographic techniques like end-to-end encryption (E2EE), digital signatures, and public key infrastructure (PKI). E2EE ensures that only the sender and receiver can read the contents of a message, preventing intermediaries from accessing sensitive data. Digital signatures authenticate message integrity, verifying that the content has not been altered during transmission. PKI manages encryption keys and certificates to ensure secure exchanges between users and organizations. Popular applications like WhatsApp, Signal, and ProtonMail use these technologies to provide secure messaging and email services.
In critical sectors like military, healthcare, and finance, secure communication is essential to protect confidential data and comply with regulations. Protocols like IPsec (Internet Protocol Security) secure data over networks, while Secure/Multipurpose Internet Mail Extensions (S/MIME) encrypts and signs emails. Emerging technologies like quantum encryption offer future-proof security against advanced cyber threats. As cyberattacks grow more sophisticated, organizations continuously upgrade their secure communication methods to ensure data privacy, user trust, and regulatory compliance.

Comments