Cloud Security
1. what is Blockchain Security?

Blockchain Security refers to the measures and practices used to protect blockchain networks, data, and transactions from attacks, fraud, and unauthorized access. Since blockchain is a decentralized and immutable system, security is critical to maintain its integrity and trustworthiness. Blockchain uses cryptographic algorithms, consensus mechanisms, and peer-to-peer networks to ensure data security. However, vulnerabilities can arise from smart contract bugs, 51% attacks, and private key theft, making security protocols essential. By implementing multi-factor authentication (MFA), data encryption, and audits, organizations can safeguard their blockchain systems against cyber threats.
One key feature of blockchain security is the consensus mechanism, which verifies and records transactions without a central authority. Common mechanisms include Proof of Work (PoW) and Proof of Stake (PoS). These ensure that only valid transactions are added to the blockchain. Furthermore, cryptographic hashing protects data integrity by converting transaction details into unique fixed-length outputs, which makes tampering nearly impossible. Private and public key encryption also ensures that only authorized users can access or transfer assets, securing digital wallets and user identities.
Blockchain security continues to evolve with innovations like zero-knowledge proofs (ZKP) for privacy preservation, multi-party computation (MPC) for secure collaboration, and quantum-resistant algorithms to protect against future threats. Organizations adopt smart contract audits, node monitoring, and threat intelligence to prevent breaches. Blockchain security is crucial in industries like finance, supply chain, and healthcare, where data integrity and privacy are paramount. As blockchain adoption grows, maintaining robust security practices is essential to protect assets and ensure trust in decentralized ecosystems.
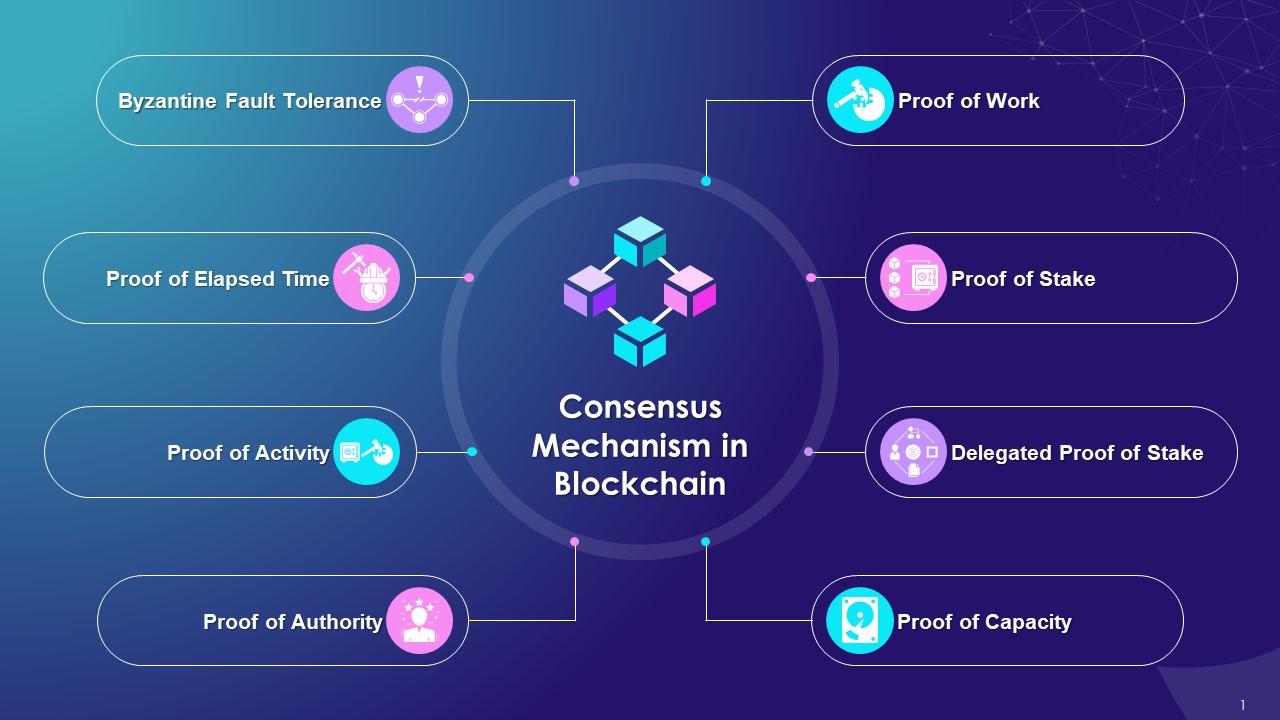
2.Consensus Mechanisms
Consensus Mechanisms are protocols used in blockchain and distributed systems to ensure that all nodes (computers) in the network agree on the validity of transactions and the state of the ledger. Since blockchains operate without a central authority, consensus mechanisms play a crucial role in maintaining trust, security, and accuracy across the system. These mechanisms prevent issues like double-spending, where the same digital asset is used more than once, and ensure that only legitimate transactions are added to the blockchain. Different consensus models offer trade-offs in speed, energy consumption, and security, depending on the system's needs.
One of the most widely known consensus mechanisms is Proof of Work (PoW), used by Bitcoin. In PoW, miners solve complex mathematical puzzles to validate transactions and add new blocks. This process is energy-intensive but provides robust security against attacks. Another popular mechanism is Proof of Stake (PoS), where validators are chosen to confirm transactions based on the amount of cryptocurrency they hold and lock as a stake. PoS is more energy-efficient and faster than PoW, making it a preferred choice for modern blockchains like Ethereum 2.0.
Other advanced consensus mechanisms include Delegated Proof of Stake (DPoS), where users vote for a limited number of trusted delegates to validate transactions, enhancing scalability. Proof of Authority (PoA) relies on pre-approved validators, making it suitable for private blockchains. Byzantine Fault Tolerance (BFT) systems, like Practical Byzantine Fault Tolerance (PBFT), ensure consensus even if some nodes act maliciously. As blockchain technology evolves, new consensus models are being developed to improve efficiency, scalability, and security, addressing the growing demands of decentralized applications (DApps) and digital ecosystems.
3. 51% Attack
51% Attack is a security threat in blockchain networks where a malicious group or individual gains control of more than 50% of the network’s mining power or computational resources. This dominance allows them to manipulate the blockchain by modifying transactions, double-spending coins, and preventing new transactions from being confirmed. It poses a significant risk to blockchains that use Proof of Work (PoW), like Bitcoin, because these networks rely on decentralized consensus to maintain trust and integrity.
When attackers control 51% or more of the network, they can reverse recent transactions, enabling them to spend the same cryptocurrency multiple times (double-spending). This undermines the immutability of the blockchain. Additionally, they can halt new transactions, effectively disrupting the normal operation of the blockchain. However, a 51% attack cannot alter past transactions, steal funds from other wallets, or bypass the blockchain’s underlying cryptography.
While large, well-established blockchains like Bitcoin are less vulnerable to 51% attacks due to their high computational power requirements, smaller blockchains with fewer miners face a greater risk. Implementing security measures such as Proof of Stake (PoS) consensus, increasing network participants, and monitoring hash rate fluctuations helps protect against these attacks. As blockchain technology evolves, researchers continue to develop new defenses to mitigate the threat of 51% attacks and preserve the integrity of decentralized systems.

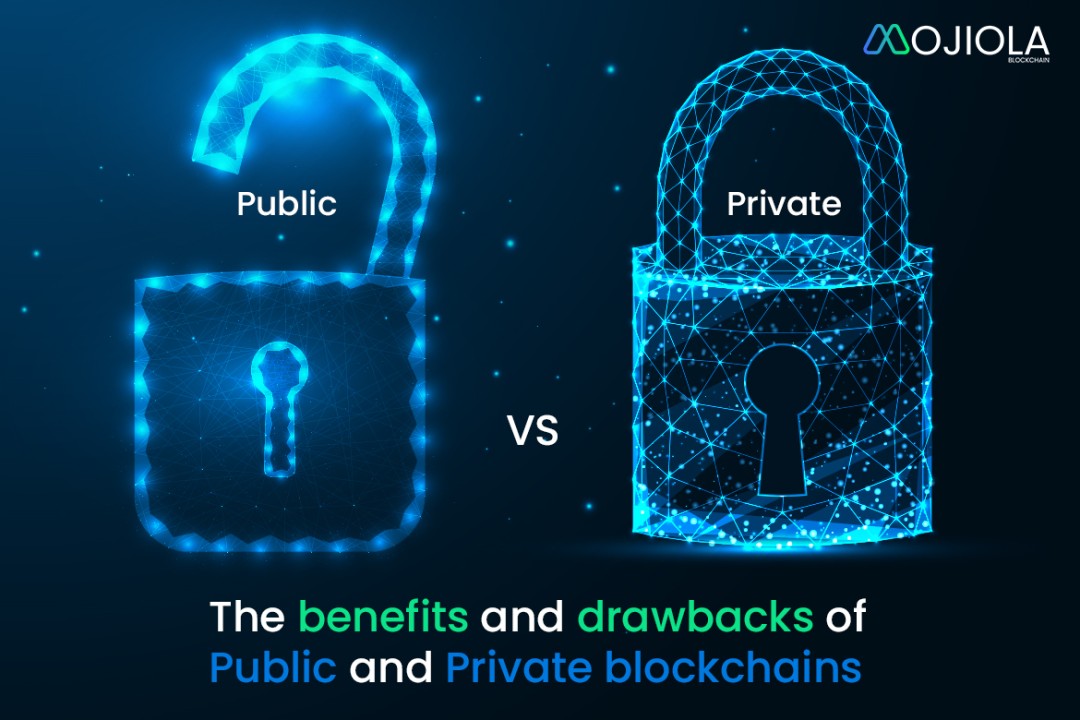
4.Private vs Public Blockchain
Private vs Public Blockchain A public blockchain is a decentralized network that is open to anyone who wants to join, read, or participate. Examples include Bitcoin and Ethereum, where anyone can verify transactions and contribute to maintaining the network. Public blockchains use consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS) to validate transactions, ensuring transparency and security. However, public blockchains can be slower and require higher energy consumption due to their open and competitive nature.
In contrast, a private blockchain is a restricted and permissioned network where only authorized users can access, read, or validate transactions. These blockchains are often used by businesses and organizations for internal purposes like supply chain management and financial transactions. They offer faster transaction speeds, better privacy, and greater control, but at the cost of reduced decentralization and potential central authority risks..
While public blockchains prioritize transparency, security, and community-driven governance, private blockchains focus on speed, efficiency, and privacy. Hybrid models, like consortium blockchains, combine features of both, allowing multiple organizations to share control while maintaining restricted access. Both models have their unique benefits, depending on the use case—public blockchains for open systems and private blockchains for enterprise solutions requiring confidentiality and efficiency.
5.Key Management
Key Management is the process of generating, distributing, storing, using, and disposing of cryptographic keys to ensure the security of sensitive information. It is a critical part of cryptography and data protection systems. Effective key management helps to protect data from unauthorized access, modification, and loss, ensuring data confidentiality, integrity, and availability. It involves managing different types of keys such as encryption keys, digital signature keys, and authentication keys, each serving specific security purposes.
A robust key management system (KMS) follows best practices like secure key generation using random number generators, safe storage through hardware security modules (HSMs), and regular key rotation to reduce risks from compromised keys. Access to keys is typically restricted to authorized users through access control policies, and audit logs track key usage for compliance and monitoring. This helps in maintaining security standards such as GDPR, HIPAA, and PCI-DSS.
Key management is essential in environments like cloud computing, blockchain, and financial systems where sensitive data needs protection. For instance, in blockchain technology, public and private key pairs secure transactions, while in cloud environments, encryption keys protect stored data. Organizations use automated key management systems to handle lifecycle tasks, improving both security and operational efficiency while minimizing human errors.

6.Secure Transactions
Secure Transactions refer to the safe exchange of data, money, or information over digital platforms while ensuring confidentiality, integrity, and authenticity. These transactions are protected using encryption techniques that safeguard sensitive data from unauthorized access during transmission. For example, SSL/TLS protocols encrypt data between a user’s browser and a website, preventing eavesdropping or tampering. Secure transactions are critical for online banking, e-commerce, and financial systems, where protecting customer information is essential.
Key components of secure transactions include encryption, authentication, and non-repudiation. Encryption ensures that data is scrambled during transfer, making it unreadable without a decryption key. Authentication verifies the identity of users through methods like passwords, biometrics, or multi-factor authentication (MFA). Non-repudiation means that a sender cannot deny having sent a transaction, which is enforced using digital signatures or blockchain technology.
Technologies such as blockchain enhance transaction security by providing a decentralized ledger that records transactions immutably, ensuring trust and transparency. Additionally, tokenization is used in payment systems, replacing sensitive information with unique identifiers. These measures protect against common threats like data breaches, man-in-the-middle attacks, and payment fraud, ensuring secure and reliable digital transactions.

7. Blockchain Forensics
Blockchain Forensics Secure transactions refer to the safe exchange of data, money, or information over digital platforms while ensuring confidentiality, integrity, and authenticity. These transactions are protected using encryption techniques that safeguard sensitive data from unauthorized access during transmission. For example, SSL/TLS protocols encrypt data between a user’s browser and a website, preventing eavesdropping or tampering. Secure transactions are critical for online banking, e-commerce, and financial systems, where protecting customer information is essential.
Key components of secure transactions include encryption, authentication, and non-repudiation. Encryption ensures that data is scrambled during transfer, making it unreadable without a decryption key. Authentication verifies the identity of users through methods like passwords, biometrics, or multi-factor authentication (MFA). Non-repudiation means that a sender cannot deny having sent a transaction, which is enforced using digital signatures or blockchain technology.
Technologies such as blockchain enhance transaction security by providing a decentralized ledger that records transactions immutably, ensuring trust and transparency. Additionally, tokenization is used in payment systems, replacing sensitive information with unique identifiers. These measures protect against common threats like data breaches, man-in-the-middle attacks, and payment fraud, ensuring secure and reliable digital transactions.

8. Smart Contract Vulnerabilities
Smart Contract Vulnerabilitiesare security weaknesses or flaws in the code of smart contracts that can be exploited by attackers to manipulate transactions, steal funds, or disrupt operations. Since smart contracts are immutable once deployed on a blockchain, any vulnerability can lead to permanent damage if not identified and fixed beforehand. Common vulnerabilities arise due to coding errors, improper logic implementation, and external dependencies. For example, the DAO hack in 2016 led to a loss of $60 million due to a reentrancy vulnerability.
One of the most critical vulnerabilities is reentrancy, where an attacker repeatedly calls a function before the previous call is completed. This can drain funds from the contract. Another issue is integer overflow and underflow, where arithmetic calculations exceed the storage limits, allowing attackers to manipulate balances. Access control flaws occur when sensitive functions are improperly restricted, enabling unauthorized users to alter the contract. Gas limit vulnerabilities can cause smart contracts to fail when exceeding the blockchain’s computational limit, leading to incomplete transactions.
To mitigate these vulnerabilities, developers use secure coding practices like input validation, proper access control, and reentrancy guards. Formal verification tools mathematically check the contract's logic for correctness. Auditing by security experts before deployment helps identify potential flaws. Implementing fail-safe mechanisms like circuit breakers can pause operations if abnormal behavior is detected. Regular code reviews, unit testing, and following security standards (e.g., OpenZeppelin libraries) are essential to minimize risks and ensure smart contract safety.

Comments